Working on WebRTC? You developed a real-time audio-video app within some hours. You tested lots on your devices, test with roommates. Everything is going as expected. But out of nowhere, it did not work with your friend in distance, nor you can talk with your family back home. How can the perfect working app for local development stop working on the production? We are missing something on the equation. Let's get started.
What is WebRTC?
WebRTC allows access to devices. You can access the microphone of your device, the camera that you have on your phone or laptop. It captures the data in real-time and can be streamed to the remote peer.
An RTCPeerConnection instance allows an application to establish peer-to-peer communications with another RTCPeerConnection instance in another browser, or to another endpoint implementing the required protocols.
Even WebRTC is a peer-to-peer connection, it required servers, to pass signalling information (to establish a connection). WebRTC has not defined any signalling protocol on itself, users can use a service of their choice.
WebRTC tries to find the best path for connection using the host address obtained from a device's operating system. If not possible it tries to find an external address using a STUN server and, if that fails, traffic is routed through a TURN relay server. This is why your app works on the local network and not on the internet.
What is NATs?
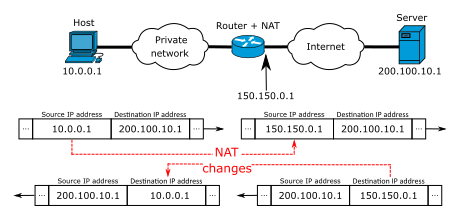 |
| Image by Michel Bakni - license CC BY-SA 4.0 |
STUN
STUN is on the public internet, the apps can use STUN server to discover its IP:port from a public perspective. STUN server simply check the IP:Port of the incoming request and response it back, there is not much work there is so not much powerful server is required.
TURN
Setup STUN and TURN server on Ubuntu
We will be using coturn, free open-source implementation of TURN and STUN Server, evolved from rfc5766-turn-server project with additional new advanced features.
Prerequisites:
- Domain with DNS management access
- A Ubuntu Server
> sudo apt-get -y update
> sudo apt-get upgrade
> sudo reboot
Let's install. coturn starts automatically once installed, so let's stop it as well.
> sudo apt-get install coturn
> sudo systemctl stop coturn
SSL certificates
We need SSL certificate to configure out TURN server, so let's generate the SSL certificate using Let's Encrypt.
> sudo apt install certbot python3-certbot-nginx
Now, let's obtain the SSL certificate. Remember before this step, you should point your domain to this server. To do so find the IP address of this server and create A record on your DNS server for name stun and turn.
Remember to Enable port 80 and 443 on inbound security rules.
eg.
Name: stun.bloggernepal.com
Record Type: A,
Pointing to: (IP address)
> sudo certbot --nginx -d stun.bloggernepal.com -d turn.bloggernepal.com
> sudo certbot renew --dry-run
The first command obtain the certificate for the domains and place them on
cert=/etc/letsencrypt/live/stun.bloggernepal.com/cert.pem
pkey=/etc/letsencrypt/live/stun.bloggernepal.com/privkey.pem
coturn configurations
> sudo nano /etc/default/coturn
and remove the # before TURNSERVER_ENABLED and press Ctl+O (write).
First, let's save the current configuration, in case we want to look through the structure later.
> sudo mv /etc/turnserver.config /etc/turnserver.config.save
Now paste the following to /etc/turnserver.conf
> sudo nano /etc/turnserver.config
1 41 42 43 44 45 46 47 48 | # /etc/turnserver.conf # STUN server port is 3478 for UDP and TCP, and 5349 for TLS. |
Everything is set by Now, let's start the coturn
> sudo systemctl start coturn
Remember to Enable port 3478 and 5349 for TCP and UDP incoming connection.
Testing STUN and TURN server
If you test a STUN server, it works if you can gather a candidate with type "srflx". If you test a TURN server, it works if you can gather a candidate with type "relay".






4 Comments
Hello sir
ReplyDeletevanakam da mapla
DeletePlease sir make full course in webrtc
ReplyDeleteHi, the test give me errors
ReplyDelete